In this article the technique of training in the method of the analysis of hierarchies (MAH) is considered. The algorithm of teaching is constructed: need of this method, discussion of a classical example, the formal description of a method, discussion of an available example about a photocopier choice, fixing on an example about a software choice on information security, independent performance of laboratory work. In the developed contents which «Information security» is considered in discipline, is present methods of an optimum choice of hardware-software systems on information security for which it is possible to use various methods including a method of the analysis of hierarchies.
In modern scientific researches the method of the analysis of hierarchies finds reflection in the solution of problems of information security and information security. S. V. Belim, S.Yu.Belim used MAI for creation of a role security policy [1], E. A. Rakhimov in model and methods of support of decision-making in intellectual system of information security [2], M. O. Chusavitin for an assessment of risks of information security of educational institution [3]. The considered method is applied widely by foreign scientists [4, 5, 6, 7]. For future expert in the field of information technologies the method of the analysis of hierarchies represents the instrument of system approach for decision-making in difficult situations of a choice of program and technical systems, technological products, etc. Therefore training in the considered approach represents a methodical problem. For a method explanation well I recommended the example offered T. Saati [8] about illumination of chairs. We will bring him. Let A, B, S and D designate the chairs placed in a straight line, conducting from a light source. We will create a scale of priorities of relative illumination for chairs. Judgments are made by the person standing near a light source which, for example, ask: «Illumination of a chair B in comparison with C is how stronger?" He answers one of the numbers for comparison which are written down in the table, and this judgment is brought in a position (In, C) matrixes. Under the agreement comparison of force is always made for the action or object standing in the left column in relation to the action or object standing in the top line. As a result we will construct a matrix of paired comparisons for four lines and four columns. The author suggests to give an idea of a method of the analysis of hierarchies without preliminary formal description, at once passing to creation of the table (tab. 1) and giving, as a priori, the set criteria of comparison.
Table 1
Matrix of paired comparisons of illumination of chairs
|
|
A |
B |
C |
D |
|
A |
|
|
|
|
|
B |
|
|
|
|
|
C |
|
|
|
|
|
D |
|
|
|
|
Further are set in an example of comparison of A and B, as numbers. When filling the table with concrete values it is worth mentioning that in this example the word is «more important», it is possible to interpret as «more lit». When comparing criterion with itself to be put 1, respectively the main diagonal is filled with units. Inverse values 1/9, 1/7, 1/5, 1/3 are brought when comparing B with A. The following options of interpretation of the word «more important» as «having bigger influence» are still possible, «more probable», is «more preferable» (table 2).
Table 2
The filled matrix of paired comparisons of illumination of chairs
|
|
A |
B |
C |
D |
|
A |
1 |
5 |
6 |
7 |
|
B |
1/5 |
1 |
4 |
6 |
|
C |
1/6 |
1/4 |
1 |
4 |
|
D |
1/7 |
1/6 |
1/4 |
1 |
After filling of table 2 we will consider formal part of a method. Let: A1... An — a set from n of elements; W1... Wn — correspond as follows:
Table 3
Calculation of relative power of criteria
|
|
A1 |
... |
An |
|
A1 |
1 |
... |
W1/Wn |
|
... |
... |
1 |
An |
|
An |
Wn/W1 |
... |
1 |
The assessment of the filled matrix of comparisons is made on formulas (table 4) for calculation of a vector of priorities.
Table 4
Assessment of priorities
|
|
A1 |
… |
An |
|
|
|
A1 |
1 |
... |
W1/Wn |
X1=(1*(W1/W2)*...*(W1/Wn))1/n |
weight (A1)=X1/sum(Xi) |
|
... |
... |
1 |
An |
... |
... |
|
An |
Wn/W1 |
... |
1 |
Xn=((Wn/W1)*...*(Wn/Wn-1)*1)1/n |
weight (An)=Xn/sum(Xi) |
|
|
sum(Xi) |
|
|||
Further to be brought the calculated assessment of priorities for an example with illumination (table 5).
Table 5
An assessment of priorities for an example with illumination
|
|
A |
B |
C |
D |
work |
root |
weight |
|
A |
1 |
5 |
6 |
7 |
210 |
3,81 |
0,61 |
|
B |
1/5 |
1 |
4 |
6 |
4,8 |
1,48 |
0,24 |
|
C |
1/6 |
1/4 |
1 |
4 |
0,17 |
0,64 |
0,10 |
|
D |
1/7 |
1/6 |
1/4 |
1 |
0,01 |
0,28 |
0,04 |
|
|
|
|
|
|
|
6,20 |
|
Following step: calculation of the coherence index (CI) which gives information on extent of violation of coherence.
We report that it is required to divide the received index into parameter from a special matrix of the casual indexes (CI) (table 6) which was received experimentally further.
Table 6
Casual indexes
|
Matrix size |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
|
Casual coherence |
0 |
0 |
0,58 |
0,9 |
1,12 |
1,24 |
1,32 |
1,41 |
1,45 |
1,49 |
The coherence relation (CR) as the relation of IS and the SI casual index for a matrix is calculated: OS=IS/SI. Size OS has to be about 10 % or less to be accepted. OS to 20 % is in certain cases allowed, but no more, differently additional check of the judgments which are carried out earlier is necessary.
Further we show the illustrating screenshot (figure 1)
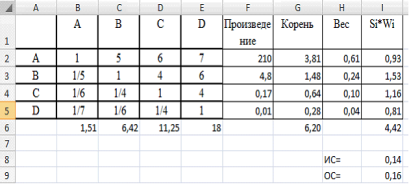
Figure 1. Result of calculations
It is possible to notice that OS turns out 16 % that demands check of judgments. The following stage in training of MAI: illustration more difficult example. The photocopier choice well is suitable for future document specialists. It is caused by that generally students aren't ready to perceive theoretically material on information security and information security as this subject is studied at the beginning of a course. Let in the market there are photocopiers, will code them numbers N1, N2, N3, N4.
We will set criteria of an assessment and system of coding:
A1 — Device cost;
A2 — Support of copying of documents of the A3 format (yes/no — 0/1);
A3 — Copying speed (low/average/high — 0/1/2);
A4 — The size (small/average/big — 0/1/2).
The author suggests to think up at once during record numerical system of comparison of qualitative criteria.
Table 7
Parameters of the chosen photocopiers and a difference assessment for comparison
|
Parameters Devices |
A1 |
A2 |
A3 |
A4 |
|
N1 |
200 |
0 |
0 |
0 |
|
N2 |
200 |
0 |
1 |
0 |
|
N3 |
500 |
1 |
1 |
1 |
|
N4 |
800 |
1 |
2 |
2 |
|
|
Difference parameter |
Difference parameter |
Difference parameter |
Difference parameter |
|
|
0–1 100–3 400–5 700–7 900–9 |
0–1 1–3 |
0–1 1–3 2–5 |
0–1 1–3 2–5 |
Table 8
Assessment of priorities
|
|
A1 |
A2 |
A3 |
A4 |
Work |
Root |
Weight |
Si*Wi |
|
A1 |
1 |
6 |
7 |
4 |
168 |
3,60 |
0,58 |
0,91 |
|
A2 |
1/6 |
1 |
4 |
3 |
2 |
1,19 |
0,19 |
1,45 |
|
A3 |
1/7 |
1/4 |
1 |
1/3 |
0,01 |
0,33 |
0,05 |
0,80 |
|
A4 |
1/4 |
1/3 |
3 |
1 |
0,25 |
0,71 |
0,11 |
0,95 |
|
Суммы |
1,56 |
7,58 |
15,00 |
8,33 |
|
5,83 |
|
4,11 |
Following step: demonstration of calculations.
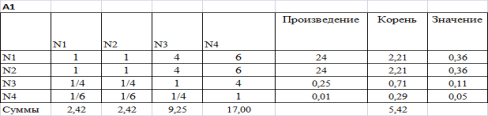
Figure 2. Result of calculations of A1
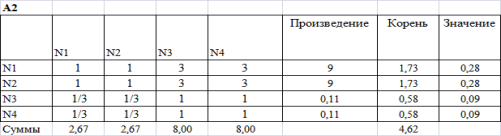
Figure 3. Result of calculations of A2
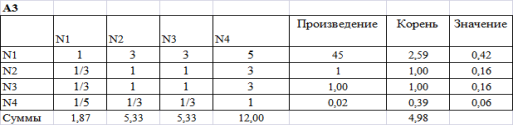
Figure 4. Result of calculations of A3
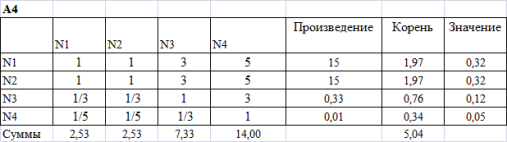
Figure 5. Result of calculations of A4
We give the reduced estimates by criteria. For receiving results it is necessary for each of devices to summarize the normalized criteria increased by the of weight.
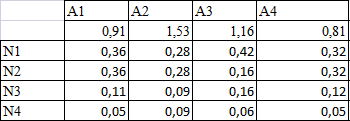
Figure 6. Summary results
As a result we receive that it is necessary to choose the N1 photocopier. The device N2 following on preference.
Further for independent study of material the task of information security and information security is given.
References:
- Bogachenko N. F., we Bleach S. V., we Bleach S. Yu. Use of a method of the analysis of hierarchies for creation of a role security policy//Problem of information security. Computer systems. 2013. No. 3. Page 7–17.
- Rakhimov E. A. Models and methods of support of decision-making in intellectual system of information security: Avtoref. … yew. Cand.Tech.Sci. Ufa, 2006
- Chusavitin M. O. Use of a method of the analysis of hierarchies at an assessment of risks of information security of educational institution//Basic researches. 2013. No. 10–9. Page 2080–2084.
- Anuar N. B., Papadaki M., Furnell S., Clarke N. Incident prioritisation using analytic hierarchy process (AHP): Rsk Index Model (RIM)//Security and communication networks. 2013. 6 (9). P. 1087–1116.
- Li B., Chang X. Application of Analytic Hierarchy Process in the Planning of Energy Supply Network for Electric Vehicles//Energy Procedia. 2011. 12(3). P. 1083–1089.
- Liu Q., Zhang Y., Kong Y., Wu Q. Improving VRSS-based vulnerability prioritization using analytic hierarchy process//Journal of Systems and Software. 2012. 85(8). P. 1699–1708.
- Yoo K. E., Choi Y. C. Analytic hierarchy process approach for identifying relative importance of factors to improve passenger security checks at airports//Journal of Air Transport Management. 2006. 12(3). P. 135–142.
- Cryptoprotection software: programs for enciphering No. 1//URL: http://www.xakep.ru/post/34845/default.asp







